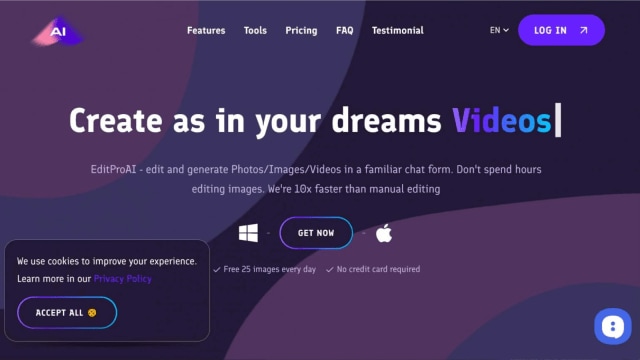
 Hackers adjacent created a morganatic looking EditPro AI website with a cooky banner astatine the bottom. (Image Source: Bleeping Computer)
Hackers adjacent created a morganatic looking EditPro AI website with a cooky banner astatine the bottom. (Image Source: Bleeping Computer)
With Artificial Intelligence powered tools disposable connected the internet, menace actors are utilizing the accidental to infect Windows and macOS-powered machines. These malware not lone bargain your cryptocurrency wallet credentials but besides people your passwords and browsing history.
According to a caller study by Bleeping Computer, menace actors are spreading malware via fake websites that impersonate an AI video and representation generator named EditPro.
In the representation below, you tin spot that the caller AI video tools are being dispersed via posts connected X, claiming that users bash not request immoderate ‘special skills’ and tin usage the AI video generators for free. The study states that clicking connected the images redirects you to a fake website offering the EditProAI tool, with ‘.pro’ and ‘.org’ domains utilized to dispersed Windows and macOS malware respectively.
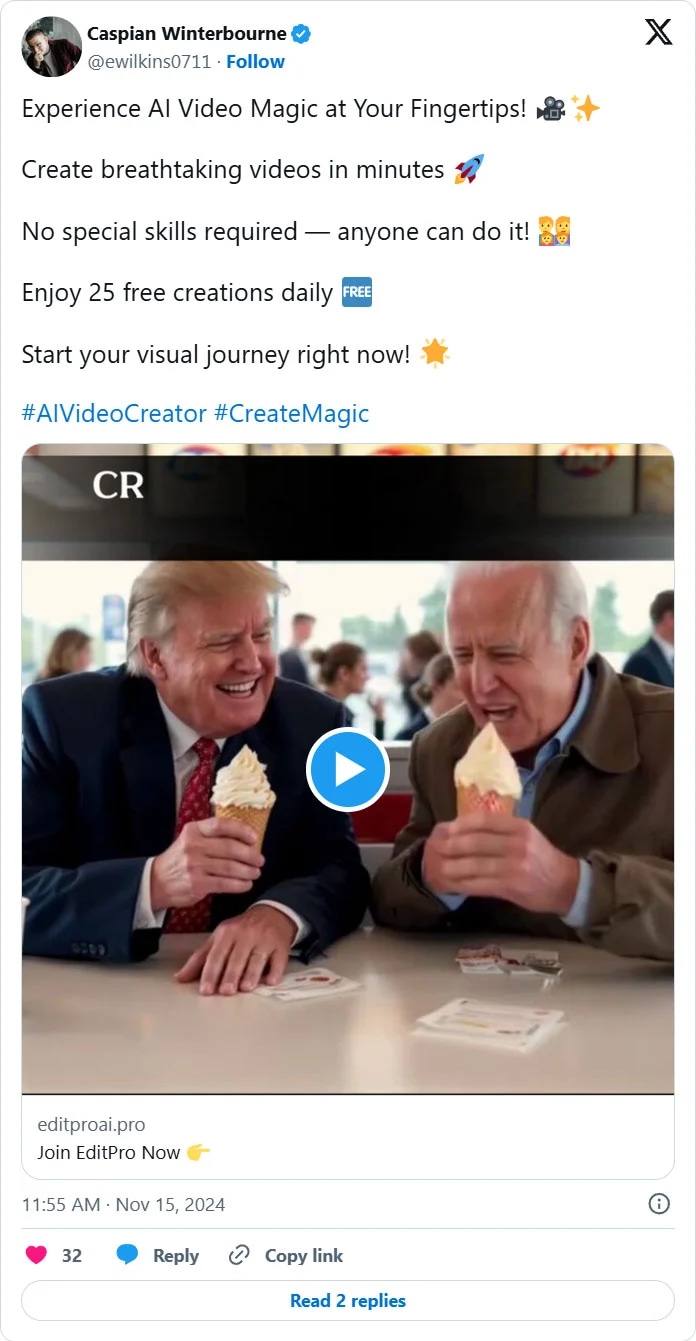 Threat actors are utilizing the EditPro AI video generator to dispersed info-stealing malware. (Image Source: Bleeping Computer)
Threat actors are utilizing the EditPro AI video generator to dispersed info-stealing malware. (Image Source: Bleeping Computer)
As it turns out, these fake websites look existent and adjacent person a cooky banner connected the bottom, which adds to the legitimacy. When users pat connected the ‘Get now’ button, your strategy volition commencement downloading a record called “Edit-ProAI-Setup-newest_release.exe” for Windows and “EditProAi_v.4.36.dmg” for macOS.
When cybersecurity experts analyzed the ‘.exe’ file, they noticed that the AI instrumentality setup was laced with the Lumma Stealer malware. In lawsuit you accidentally downloaded the program, we urge you alteration your saved passwords arsenic your accounts whitethorn person been compromised.
To springiness you a speedy recap, Lummar Stealer is simply a Windows malware portion AMOS infects devices moving macOS. However, some malware are designed to bargain cryptocurrency wallets, login credentials and browsing past from fashionable browsers similar Google Chrome, Mozilla Firefox and Microsoft Edge. The information collected is past sent backmost to the hacker, who tin past usage it for aboriginal attacks oregon merchantability it connected the acheronian web.

 2 days ago
4
2 days ago
4
















.png)

.png)
.png)
.png)













 English (US) ·
English (US) ·  Hindi (IN) ·
Hindi (IN) ·